Innovations / Solutions / Applications / Cloud-Native
AgileGuru Engineering blog on innovative solutions and technical excellence by engineers and architects.

Using Workload Identity For Password-less Security.
Guru Raghupathy, 01 January 2025
Workload Identity represents a modern, security-focused approach to managing authentication between services and workloads. This powerful helps in significantly enhancing your cloud security posture. Workload Identity creates a trust relationship between services by binding Kubernetes Service Accounts (KSAs) to Service Accounts (SAs). This binding allows pods to automatically authenticate with services using the pod's assigned Kubernetes service account, rather than requiring stored credentials.
Key Benefits
- Enhanced Security : By eliminating the need to manage and store service account keys, Workload Identity significantly reduces security risks. There are no static credentials to potentially expose or compromise, and no keys to rotate or manage.
- Simplified Operations : Operations teams no longer need to manage the lifecycle of service account keys or implement complex secret management solutions. The authentication process becomes automatic and seamless.
- Fine-grained Access Control : Workload Identity enables precise control over which pods can access specific GCP services, following the principle of least privilege. This granular control helps maintain a strong security posture while ensuring necessary access for applications.
Implementation Guide Using GCP AND GKE
1. Enable Workload Identity on Your GKE Cluster
- When creating a new cluster:
gcloud container clusters create my-cluster \
--workload-pool=PROJECT_ID.svc.id.goog \
--region=us-central1
- Change existing clusters:
gcloud container clusters update my-cluster \
--workload-pool=PROJECT_ID.svc.id.goog \
--region=us-central1
2. Create and Configure Service Accounts
- First, create a Google Service Account:
gcloud iam service-accounts create gsa-name \
--project=PROJECT_ID
- Then, create a Kubernetes Service Account:
apiVersion: v1
kind: ServiceAccount
metadata:
name: ksa-name
namespace: default
annotations:
iam.gke.io/gcp-service-account: gsa-name@PROJECT_ID.iam.gserviceaccount.com
3. Establish the Identity Binding
- Allow the Kubernetes Service Account to impersonate the Google Service Account:
gcloud iam service-accounts add-iam-policy-binding \
gsa-name@PROJECT_ID.iam.gserviceaccount.com \
--role roles/iam.workloadIdentityUser \
--member "serviceAccount:PROJECT_ID.svc.id.goog[NAMESPACE/KSA_NAME]"
4. Configure Your Workload
- Modify your pod specification to use the Kubernetes Service Account:
apiVersion: v1
kind: Pod
metadata:
name: my-pod
spec:
serviceAccountName: ksa-name
containers:
- name: main
image: my-application:latest
Best Practices
1. Namespace Isolation: Create separate service accounts for different environments and namespaces to maintain proper isolation.
2. Regular Auditing: Periodically review and audit the Workload Identity bindings to ensure they align with your security requirements.
3. Least Privilege: Grant only the necessary IAM roles to Google Service Accounts, following the principle of least privilege.
4. Documentation: Maintain clear documentation of all service account bindings and their purposes for better governance.
Common Troubleshooting Steps
1. Verify that Workload Identity is properly enabled on your cluster
2. Check that the service account annotations are correctly configured
3. Ensure IAM bindings are properly set up
4. Validate that pods are using the correct Kubernetes service account
5. Review pod logs for authentication-related errors
Jenkins Demo with seemless auth without password / credentials
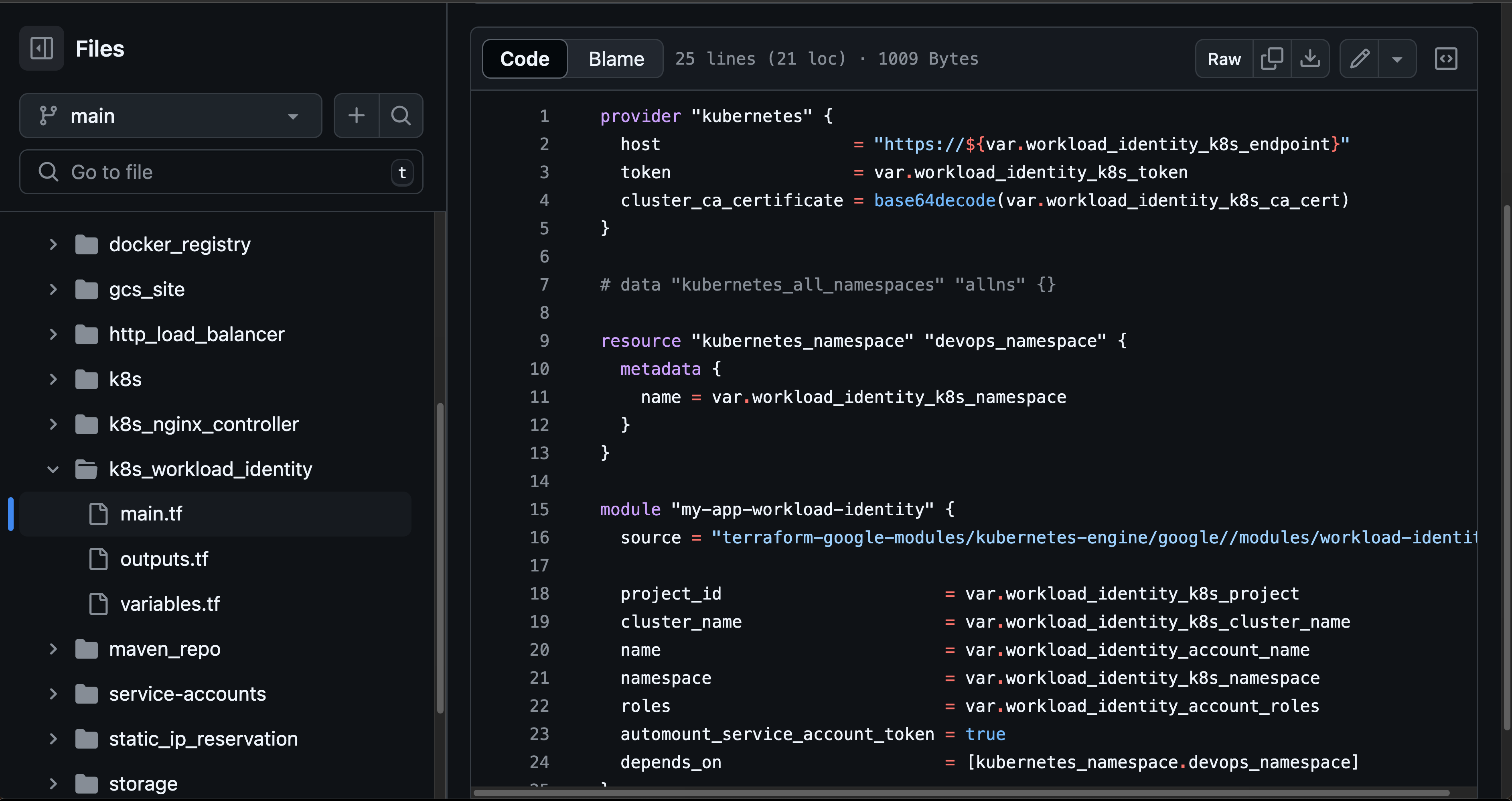
1. Terraform Setup WorkLoad Identity Module :
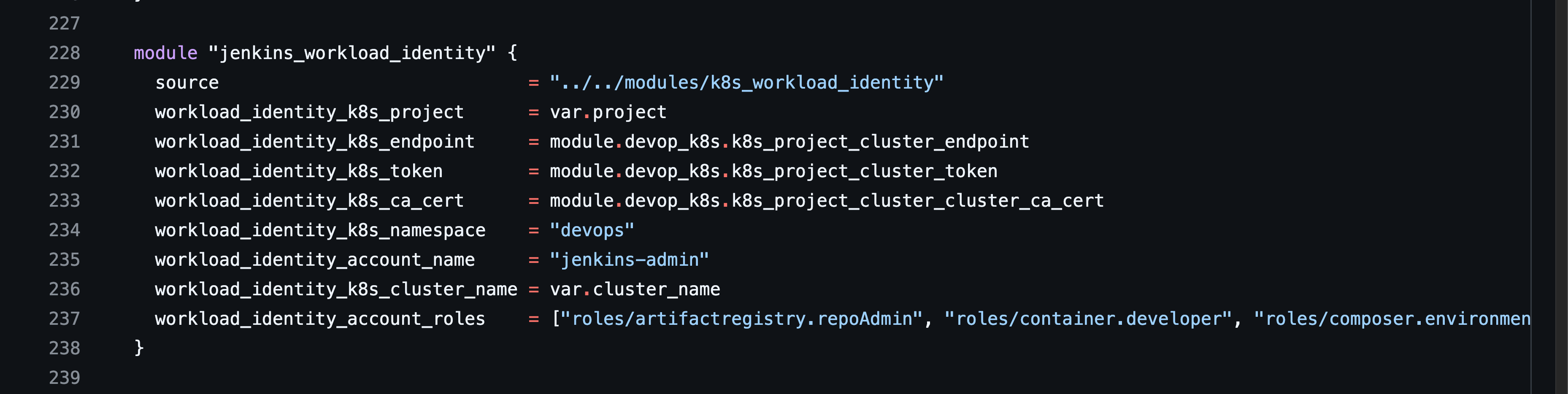
2. Terraform Make K8S Service Account WorkLoad Identity :
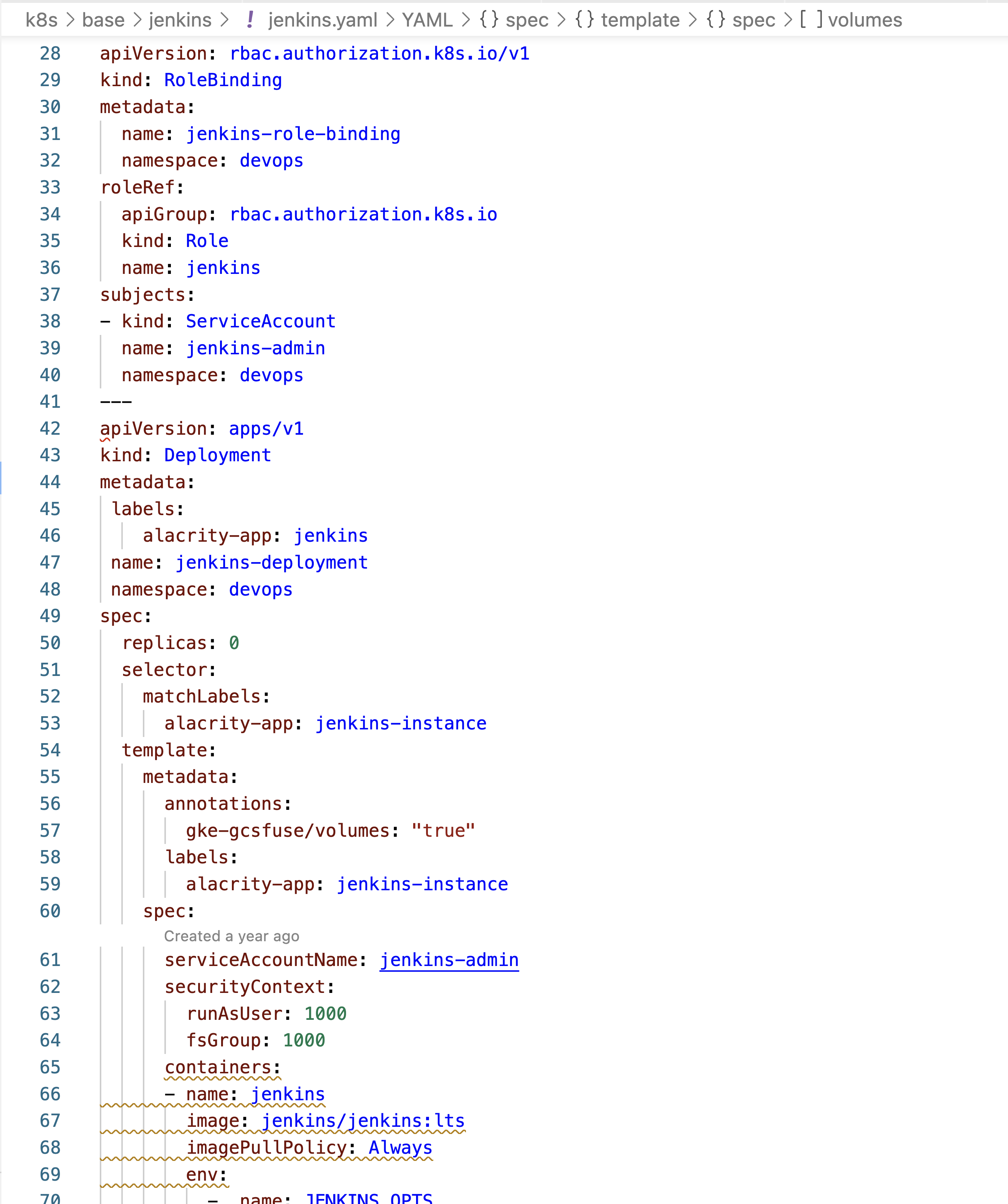
3. Terraform Setup Jenkins Service Account In Kubernetes :
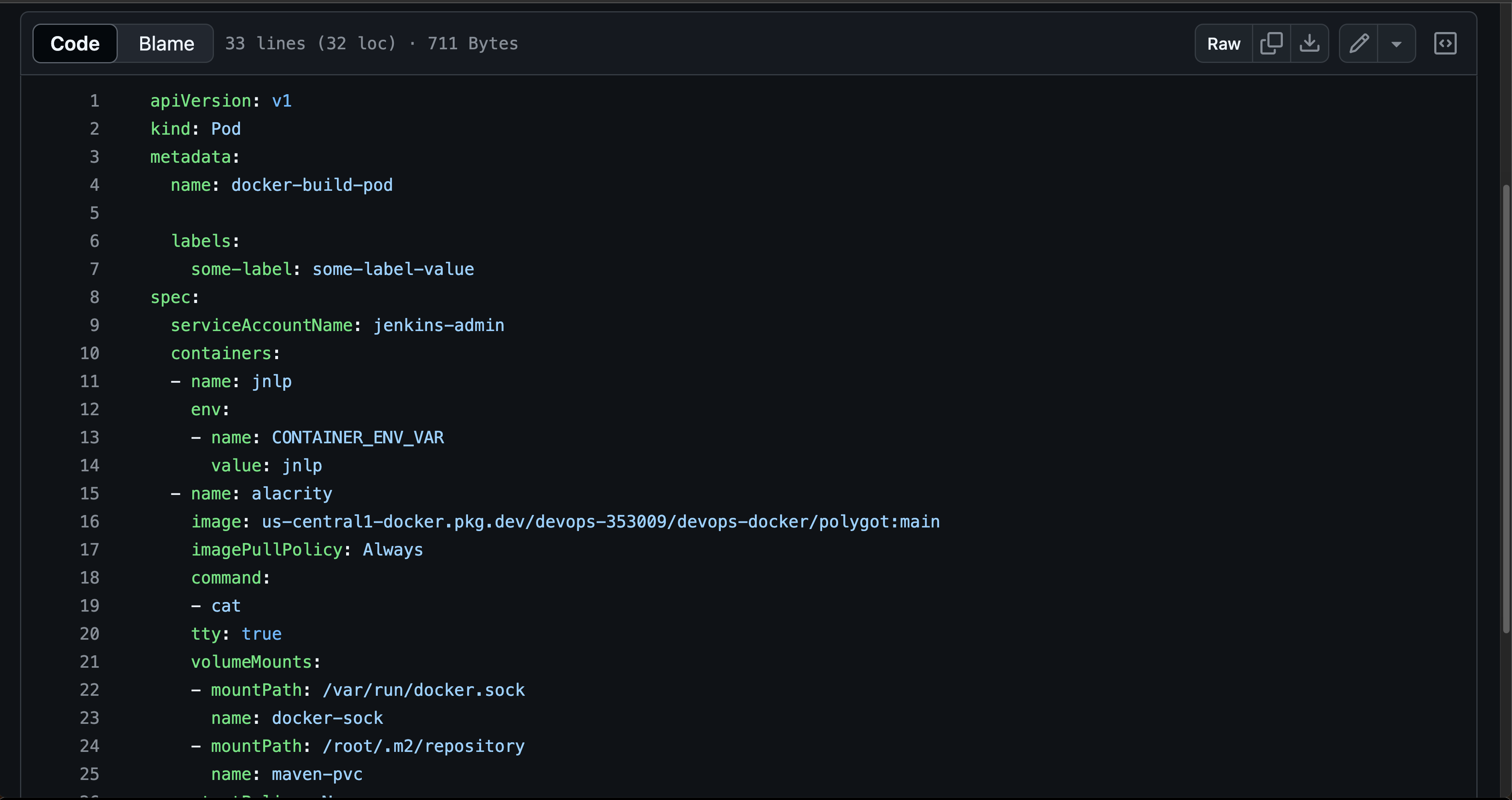
4. Terraform Setup Jenkins Pod Template :
5. Terraform Define Simple Pipeline without any password :
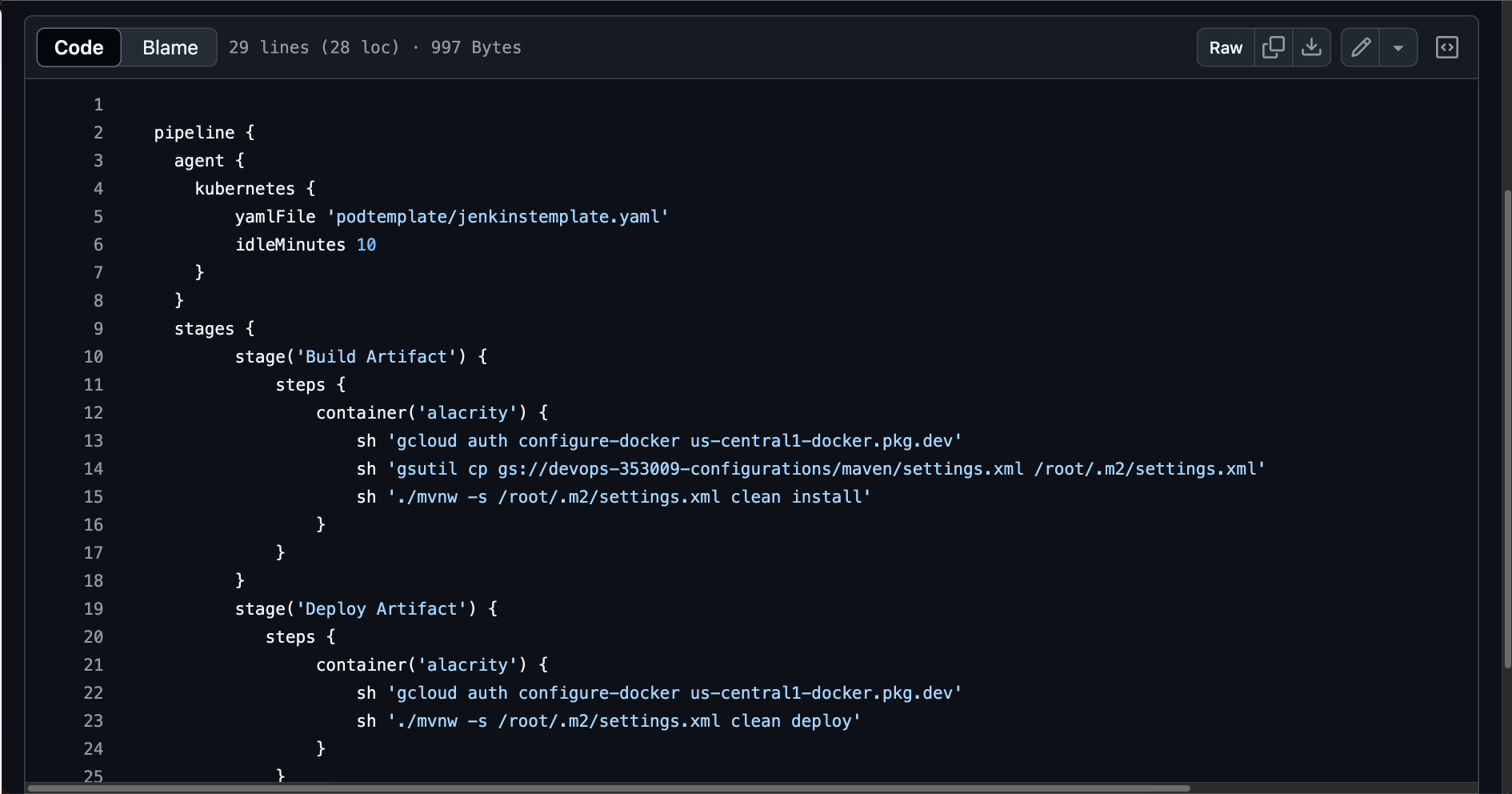
Conclusion
Workload Identity represents a significant advancement in cloud security practices, offering a more secure and manageable approach to service authentication in GKE environments. By implementing Workload Identity, organizations can enhance their security posture while simplifying operational overhead. Remember that transitioning to Workload Identity might require careful planning and testing, especially in production environments. However, the long-term benefits in terms of security and manageability make it a worthwhile investment for any organization running workloads on GKE.
Author : Guru Raghupathy , 01 January 2025